Free Public Smtp Relay
You can set up your on-premises printer, scanner, fax, or application to send email through G Suite. Depending on your requirements, the available options are:. G Suite —Send mail from your organization by authenticating with the IP addresses. You can send messages to anyone inside or outside of your domain. Gmail SMTP server—Send mail to anyone inside or outside of your domain.
This option requires you to authenticate with your Gmail or G Suite account and password. Restricted Gmail SMTP server—Send messages to Gmail or G Suite users only. This option does not require you to authenticate.Note: Our support team can't assist with configuration settings.
For details about configuring your device or application to send SMTP messages, refer to its respective documentation. Step 1: Choose your configuration optionThe following table lists the configuration options based on what’s supported by your device or application. You configure these options within the device or application.
G Suite SMTP relay (recommended)Gmail SMTP serverRestricted Gmail SMTP serverSending limitsA registered G Suite user can't relay messages to more than 10,000 recipients per day. For full SMTP relay limits, see.2,000 Messages per day.
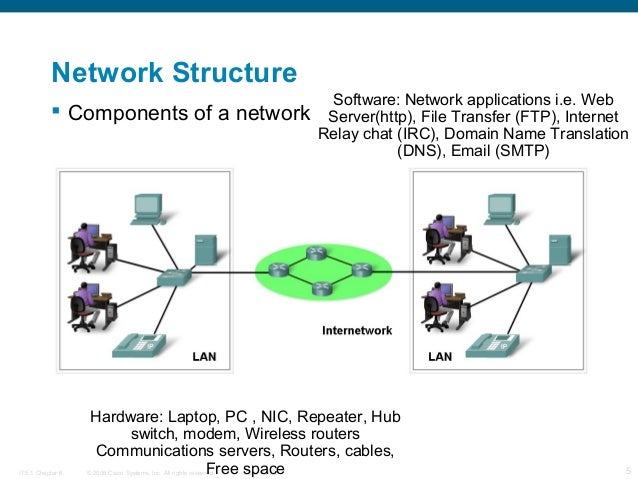
See.Per user receiving limits apply. If you connect using SSL or TLS, you can send mail to anyone with smtp.gmail.com.Note: Before you start the configuration, we recommend you set up App passwords for the the desired account. Learn more at and. Connect to smtp.gmail.com on port 465, if you’re using SSL. (Connect on port 587 if you’re using TLS.). Sign in with a Google username and password for authentication to connect with SSL or TLS. Ensure that the username you use has cleared the CAPTCHA word verification test that appears when you first sign in.
If your device or application doesn’t support SSL, you can only send mail to Gmail or G Suite users.Use the restricted SMTP server. Connect to aspmx.l.google.com on port 25. Configure an for your domain with the IP address of the device or application to ensure that recipients don’t reject mail sent from it. In your Google Admin console, add this IP address to the box.For example, if your sending device sends from 123.45.67.89, add that address to your SPF record without removing the G Suite mail servers from the record: v=spf1 ip4:123.45.67.89 include:spf.google.com all.
Contents.History and technology Until the 1990s, mail servers were commonly intentionally configured as open relays; in fact this was frequently the installation default setting. The traditional method of relaying e-mail to its destination required that it was passed from computer to computer (through and beyond the Internet) via on telephone lines. For many early networks, such as, and, lists of machines that were open relays were a core part of those networks. And speed of e-mail delivery were not priorities at that time and in any case the government and educational servers that started the Internet were covered by a federal edict forbidding the transfer of commercial messages. Abuse by spammers In the mid-1990s, with the, spammers resorted to re-routing their e-mail through third party e-mail servers to avoid detection and to exploit the additional resources of these open relay servers. Spammers would send one e-mail to the open relay and (effectively) include a large list, then the open relay would relay that spam to the entire list. While this greatly reduced the bandwidth requirements for spammers at a time when Internet connections were limited, it forced each spam to be an exact copy and thus easier to detect.
Dragon age origins zathrian. After abuse by spammers became widespread, operating an open relay came to be frowned upon among the majority of Internet server administrators and other prominent users. Open relays are recommended against in and (which defines ). The exact copy nature of spam using open relays made it easy to create bulk e-mail detection systems such as Vipul's Razor and the. To counter this, spammers were forced to switch to using to make them less effective and the advantage of using open relays was removed since every copy of spam was 'unique' and had to be sent individually.Since open mail relays make no effort to the sender of an e-mail, open mail relays are vulnerable to. Anti-spam efforts Many Internet service providers use (DNS-based Blocking Lists) to disallow mail from open relays. Once a mail server is detected or reported that allows third parties to send mail through them, they will be added to one or more such lists, and other e-mail servers using those lists will reject any mail coming from those sites. The relay need not actually be used for sending spam to be blacklisted: instead, it may be blacklisted after simple test that just confirms open access.
This trend reduced the percentage of mail senders that were open relays from over 90% down to well under 1% over several years. This led to spammers adopting other techniques, such as the use of of to send spam.One consequence of the new unacceptability of open relays was an inconvenience for some end users and certain.
To allow customers to use their e-mail addresses at Internet locations other than the company's systems (such as at school or work), many mail sites explicitly allowed open relaying so that customers could send e-mail via the ISP from any location. Once open relay became unacceptable because of abuse (and unusable because of blocking of open relays), ISPs and other sites had to adopt new protocols to allow remote users to send mail. These include, and the use of (VPNs). The has written a covering Email Submission Operations in.Note that the above only becomes an issue if the user wishes to (or has to) continue to send e-mail remotely, using the same SMTP server which they were previously accessing locally.
If they have valid access to some other SMTP server from their new, remote location, then they will typically be able to use that new server to send e-mails as if from their old address, even when this server is properly secured. (Although this may involve some reconfiguration of the user's which may not be entirely straightforward.)The makes it illegal to send spam through an open relay in the, but makes no provision on their use for personal e-mail or their operation in general; the effectiveness of the act has been questioned. Modern-day proponents The most famous open mail relay operating today is probably that of, who argues that running an open relay is a issue. His server is included on many open relay blacklists (many of which are generated by 'automatic detection', that is, by anti-spam blacklisters sending an (unsolicited) test e-mail to other servers to see if they will be relayed). These measures cause much of his outgoing e-mail to be blocked. Along with his further deliberate configuration of the server, his open relay enables people to send e-mail without their IP address being directly visible to the recipient and thereby send e-mail.
In 2002, his open relay, along with 24 others, was used by a to propagate.John Gilmore and other open relay proponents declare that they do not support spam and spamming, but see bigger threat in attempts to limit web capabilities that may block evolution of the new, next generation technologies. They compare the network communication restrictions with restrictions that some phone companies tried to place on their lines in the past, preventing transferring of computer data rather than speech. ^ The Trustees of Indiana University (2008-04-01).
University Information Technology Services. Archived from on 2007-06-17.
Retrieved 2008-04-07. ^.
Public Smtp Relay Server
Archived from on 2007-08-24. Retrieved 2008-04-07. Archived from on March 6, 2008. Retrieved 2008-04-07. Commercialization of the Internet. Aber, James S. ES 351 and 771.
Retrieved 2008-04-07. ^.
Archived from on June 1, 2008. Retrieved 2008-04-07. Hoffman, Paul (2002-08-20). IMC Reports. Archived from on 2007-01-18. Retrieved 2008-04-13.
Atkins, Steve. Archived from on 2012-07-27. Retrieved 2008-04-08. Retrieved 2008-04-07.
Retrieved 2008-04-07. ^. Archived from on February 24, 2008.
Retrieved 2008-04-12. Retrieved 2010-05-09. Retrieved 2008-10-28. Retrieved 2008-10-29.